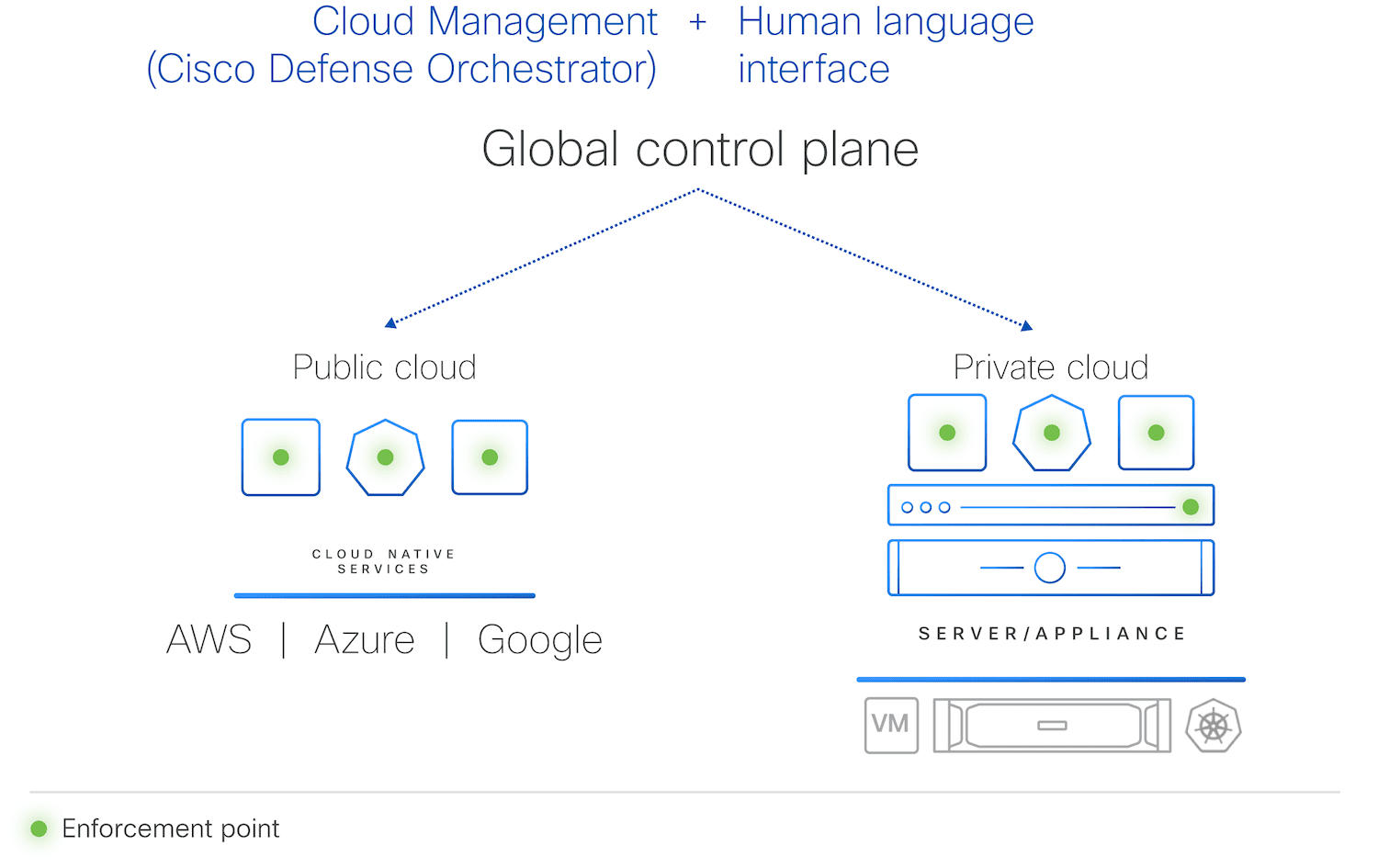
Cisco announced the debut of its groundbreaking security solution, Cisco Hypershield, specifically designed for AI-scale data center security. Revolutionizing Network Security Cisco Hypershield is the most significant security innovation in the company’s history. This cloud-native, AI-powered security system is made … Read More
Defense in Depth
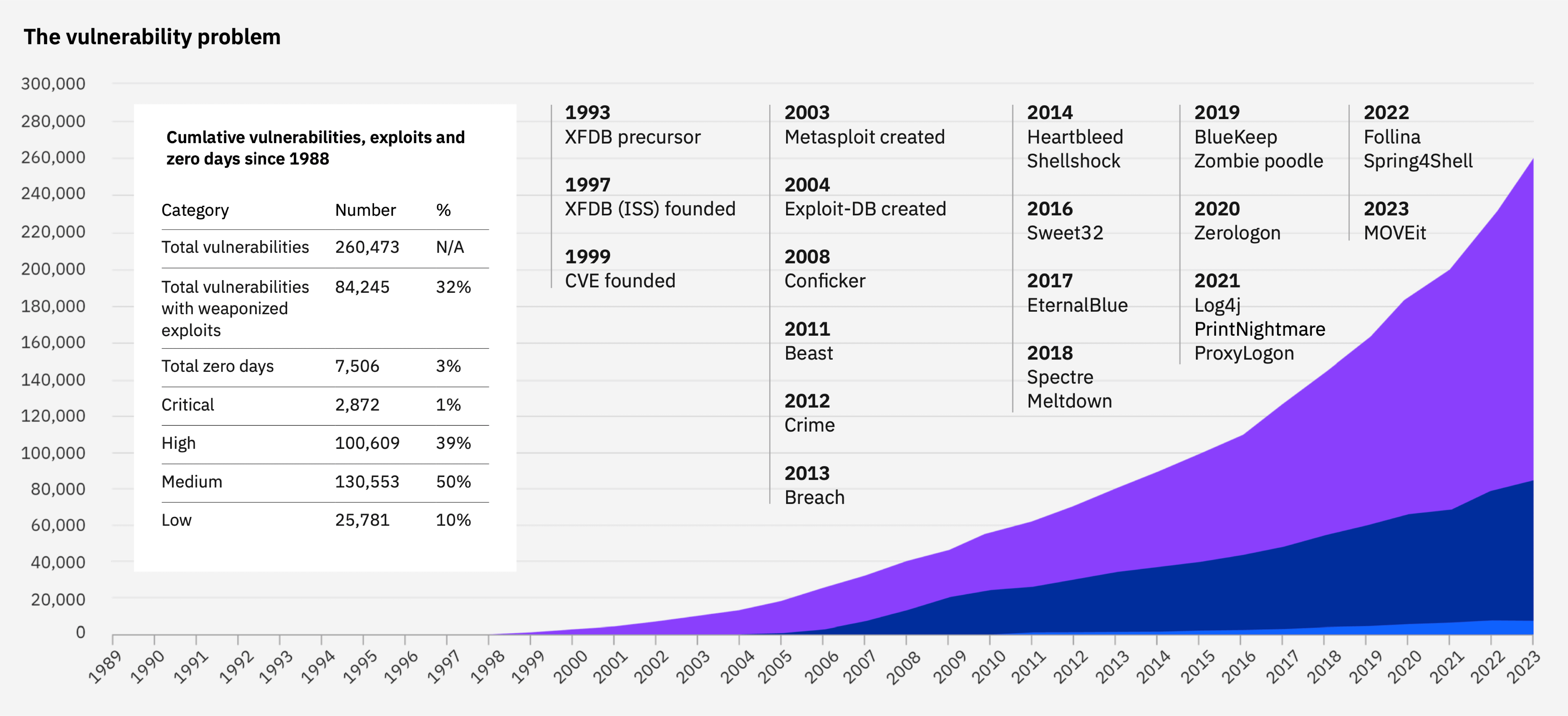
IBM X-Force Combating Cyber Threats Targeting Identities
Key Insights and Defense Strategies from IBM’s X-Force Report IBM’s latest X-Force Threat Intelligence Index highlights a surge in cyber threats targeting identities. Stolen credentials were used in 30% of cases in 2023. This marks a 71% increase from the … Read More
Securing Kubernetes with Shielded GKE Nodes
Strengthening Kubernetes Security: How Shielded GKE Nodes Protect Your Cloud-Native Infrastructure In the modern cloud-native ecosystem, Kubernetes has become a critical part of IT infrastructure for managing containerized applications. However, as the use of Kubernetes grows, so does the security … Read More
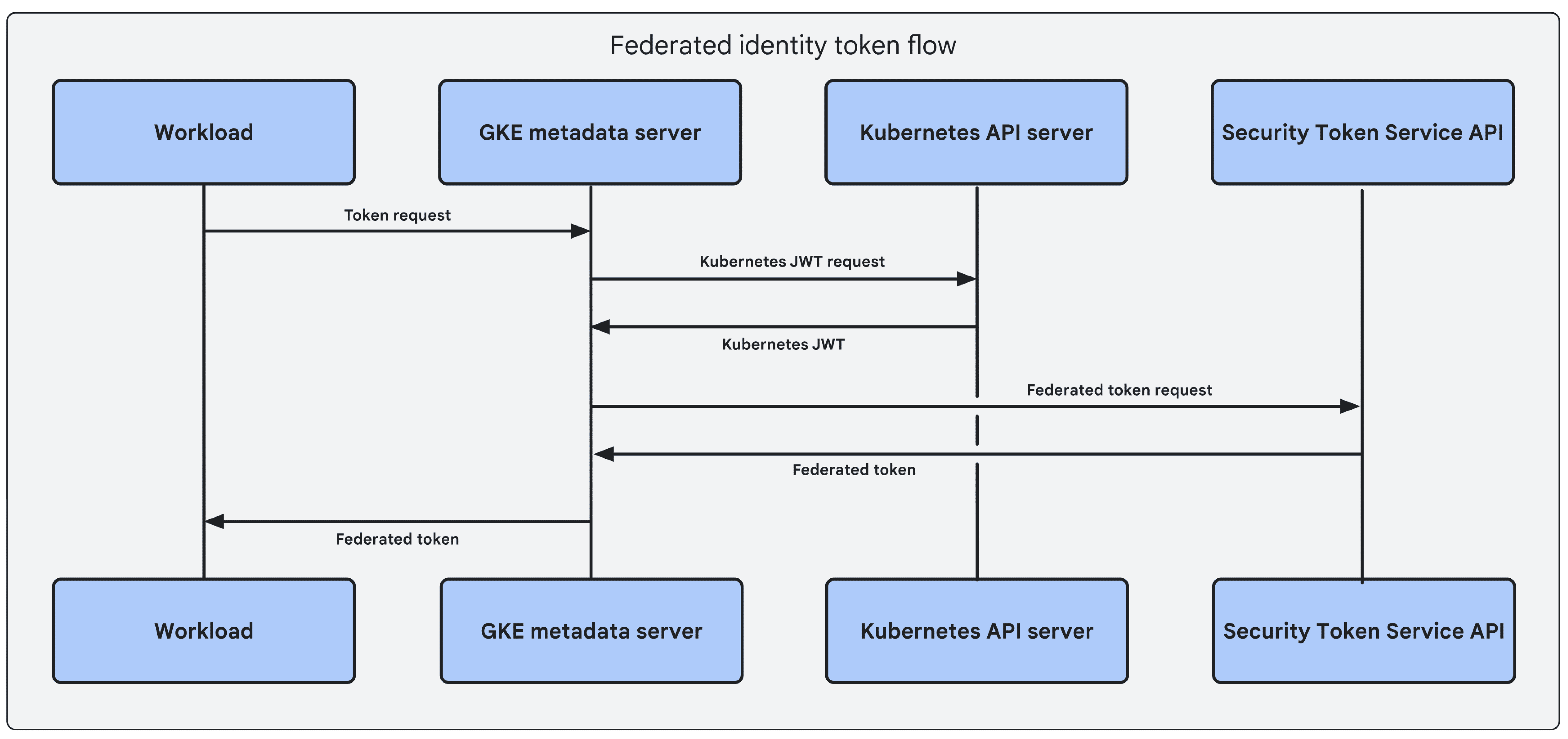
Secure Google Cloud: Identity Federation for GKE
Implementing Workload Identity Federation in Google Kubernetes Engine (GKE) for Enhanced Security and Performance In the rapidly evolving world of cloud computing, securing application access to cloud services without compromising security or flexibility is a critical challenge.Google Kubernetes Engine (GKE) … Read More

System Compromise: Recent Studies on the SolarWinds Incident
The SolarWinds system compromise, a monumental espionage event in recent history, was both intricately designed and executed. Allegedly orchestrated by hackers affiliated with a foreign government, this compromise targeted SolarWinds—a prominent IT management software provider—by infiltrating its widely utilized Orion … Read More

Securing Trust: Lessons from Banorte Cybersecurity Incident
In the evolving landscape of cybersecurity, securing trust is paramount, as evidenced by the Banorte data breaches which offer a stark reminder of the vulnerabilities that even large financial institutions can face. Through a detailed exploration of these incidents, we … Read More

Enhancing Container Security: Best Practices from Guilda
The Importance of Container Security in Cloud Computing In the rapidly evolving landscape of cloud computing, container technology stands out as a revolutionary tool that reshapes how developers build, deploy, and manage applications efficiently. As organizations increasingly adopt containers for … Read More

Guilda Cybersecurity Solutions: Empower Your Business
Seamlessly Integrate Advanced Cybersecurity with Guilda’s Expert Guide As we navigate the complexities of cybersecurity, integrating advanced cybersecurity solutions into your business operations is not just beneficial—it’s essential. Here at Guilda, we dedicate ourselves to empowering businesses with the tools … Read More