The digital landscape is rapidly evolving, with cloud computing emerging as a transformative force across industries. For businesses interacting with the U.S. government, particularly those handling sensitive data, understanding and adhering to the Federal Risk and Authorization Management Program (FedRAMP) … Read More
Cybersecurity

CrowdStrike Catastrophe: Raising Software Quality Standards
In a world increasingly reliant on digital infrastructure, the failure to release high-quality software can lead to catastrophic consequences. The recent CrowdStrike Catastrophe serves as a stark reminder of the devastating impact that unscrupulous companies, lacking proper guidance and ethics, … Read More

Understanding Legal Issues in Cloud Computing and GCP
In the era of digital transformation, understanding legal issues in cloud computing is crucial. Every organization must satisfy legal standards and regulations while using cloud computing. Adhering to standards like HIPAA, GDPR, and ISO 27018 helps in compliance. However, compliance … Read More
Governance, Risk, and Compliance in Cloud Computing and GCP
The rapid adoption of cloud computing has transformed how organizations operate, offering unparalleled agility, scalability, and cost-efficiency. However, this shift to the cloud also brings unique challenges related to governance, risk, and compliance (GRC). Properly addressing these aspects is crucial … Read More
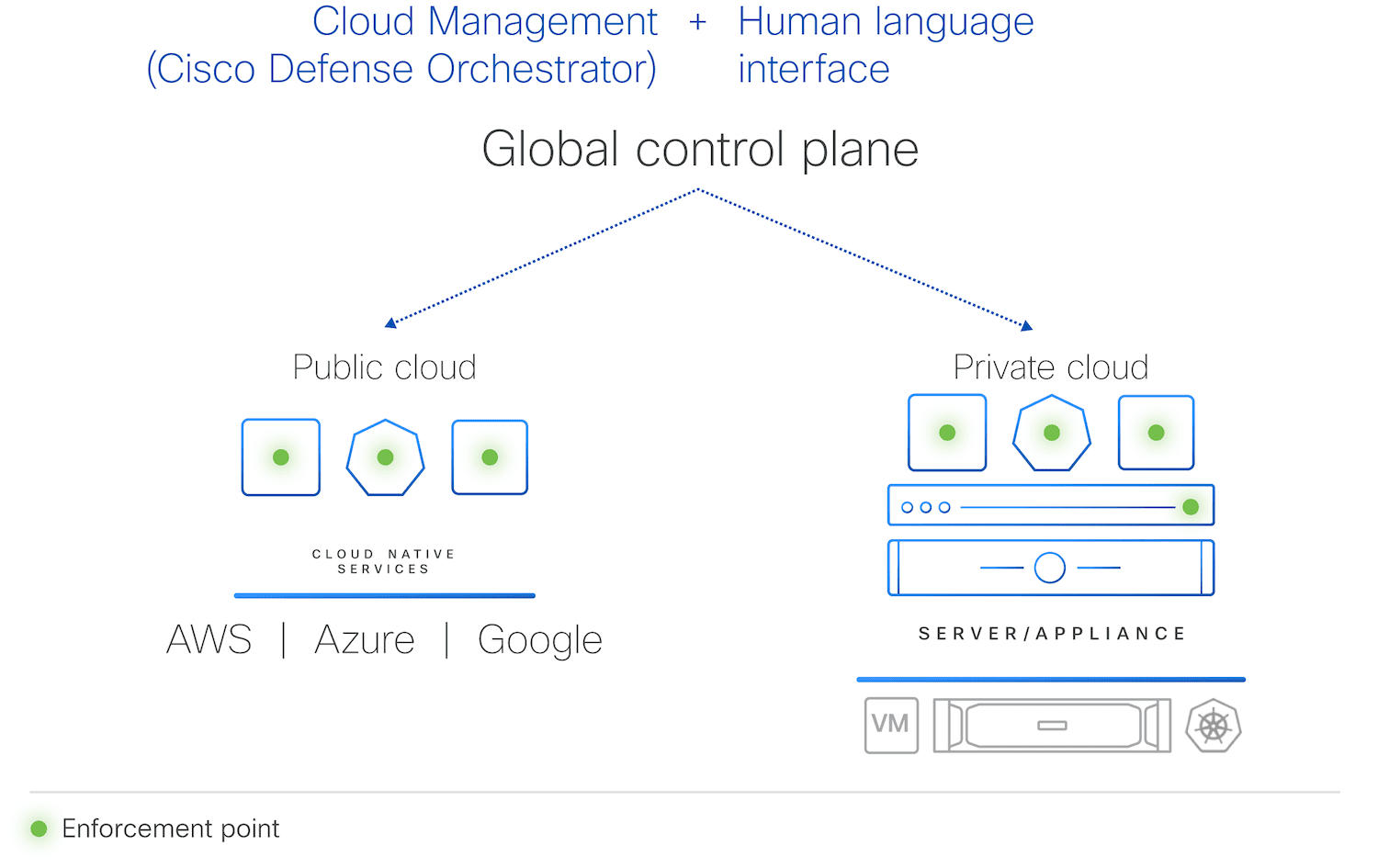
Cisco Hypershield: AI-Scale Data Center Security
Cisco announced the debut of its groundbreaking security solution, Cisco Hypershield, specifically designed for AI-scale data center security. Revolutionizing Network Security Cisco Hypershield is the most significant security innovation in the company’s history. This cloud-native, AI-powered security system is made … Read More
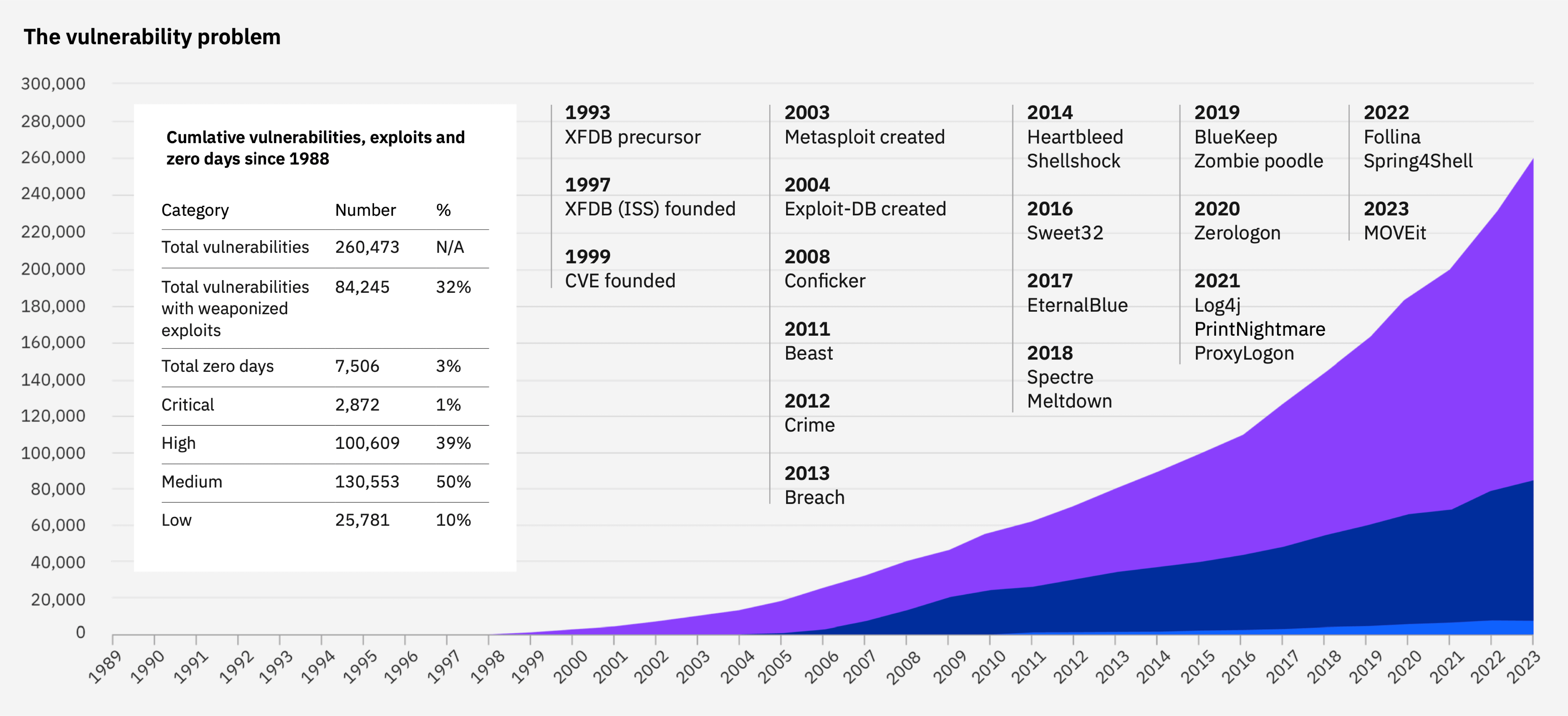
IBM X-Force Combating Cyber Threats Targeting Identities
Key Insights and Defense Strategies from IBM’s X-Force Report IBM’s latest X-Force Threat Intelligence Index highlights a surge in cyber threats targeting identities. Stolen credentials were used in 30% of cases in 2023. This marks a 71% increase from the … Read More

Sony Reports Cybersecurity Breach Affecting 6,800 Customers
Major Cybersecurity Breach at Sony: Personal Data of Employees and Families Exposed Due to Zero-Day Vulnerability Sony Interactive Entertainment has officially announced a significant cybersecurity breach affecting current and former employees and their family members, with personal information being exposed. … Read More
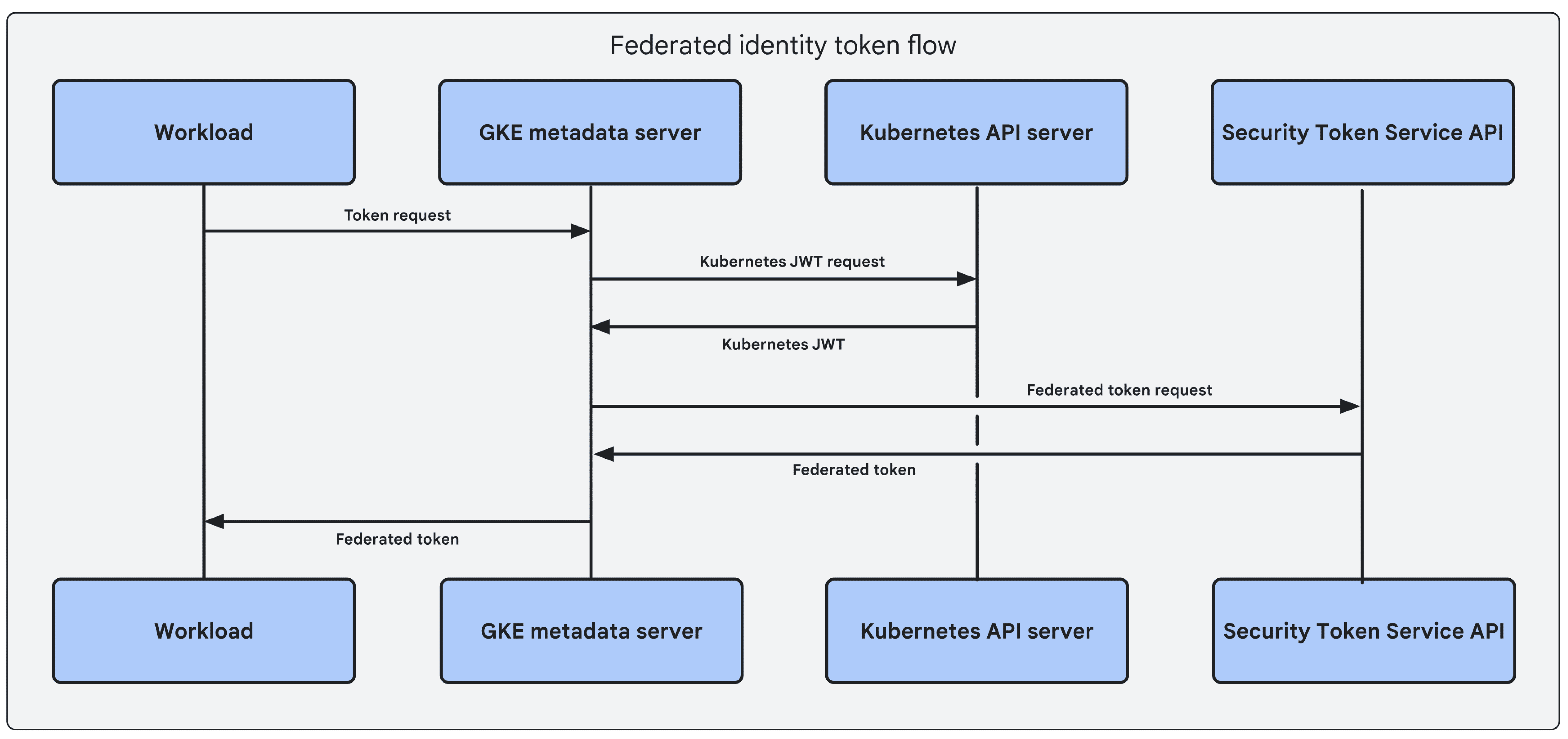
Secure Google Cloud: Identity Federation for GKE
Implementing Workload Identity Federation in Google Kubernetes Engine (GKE) for Enhanced Security and Performance In the rapidly evolving world of cloud computing, securing application access to cloud services without compromising security or flexibility is a critical challenge.Google Kubernetes Engine (GKE) … Read More

System Compromise: Recent Studies on the SolarWinds Incident
The SolarWinds system compromise, a monumental espionage event in recent history, was both intricately designed and executed. Allegedly orchestrated by hackers affiliated with a foreign government, this compromise targeted SolarWinds—a prominent IT management software provider—by infiltrating its widely utilized Orion … Read More

Securing Trust: Lessons from Banorte Cybersecurity Incident
In the evolving landscape of cybersecurity, securing trust is paramount, as evidenced by the Banorte data breaches which offer a stark reminder of the vulnerabilities that even large financial institutions can face. Through a detailed exploration of these incidents, we … Read More

