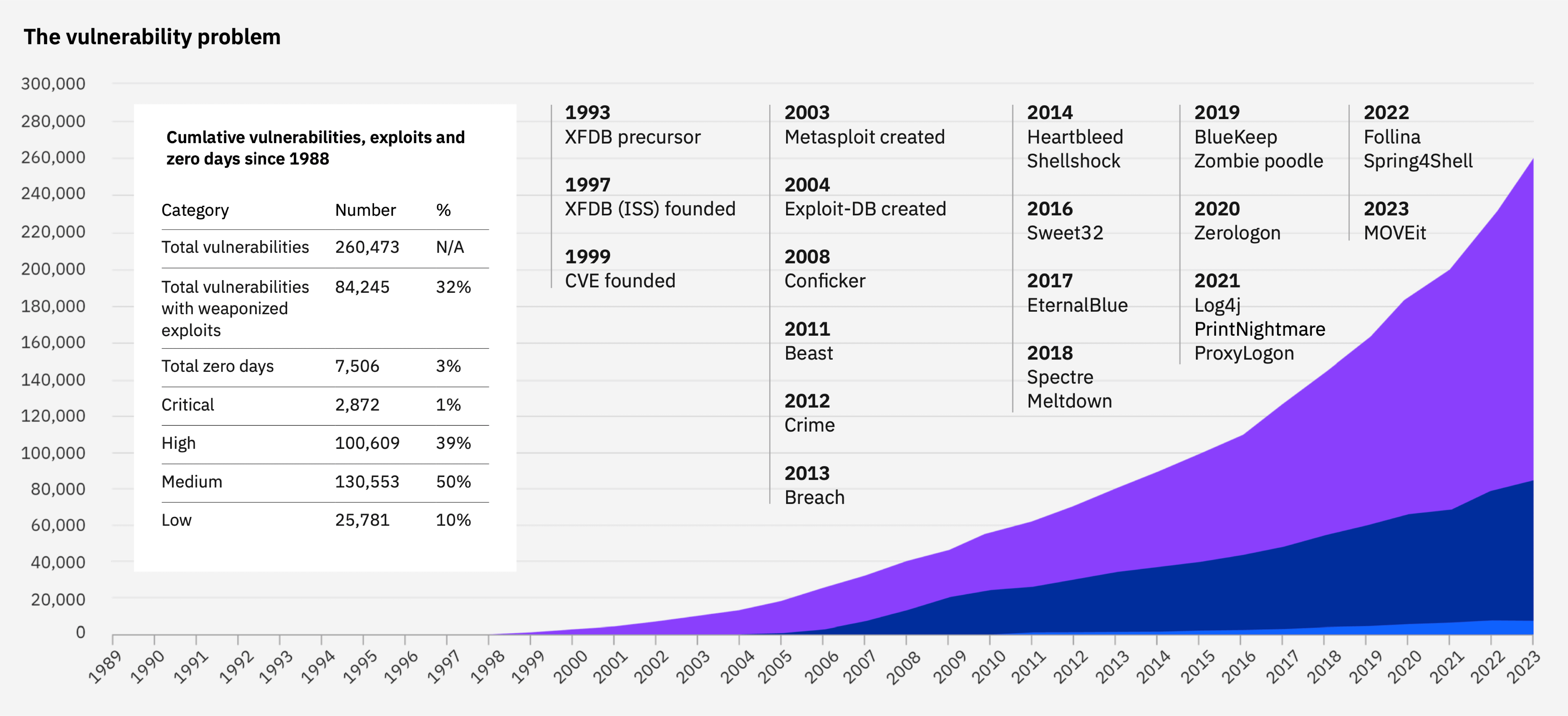
Key Insights and Defense Strategies from IBM’s X-Force Report IBM’s latest X-Force Threat Intelligence Index highlights a surge in cyber threats targeting identities. Stolen credentials were used in 30% of cases in 2023. This marks a 71% increase from the … Read More
Author Archives: Marco Villarruel

Sony Reports Cybersecurity Breach Affecting 6,800 Customers
Major Cybersecurity Breach at Sony: Personal Data of Employees and Families Exposed Due to Zero-Day Vulnerability Sony Interactive Entertainment has officially announced a significant cybersecurity breach affecting current and former employees and their family members, with personal information being exposed. … Read More
Securing Kubernetes with Shielded GKE Nodes
Strengthening Kubernetes Security: How Shielded GKE Nodes Protect Your Cloud-Native Infrastructure In the modern cloud-native ecosystem, Kubernetes has become a critical part of IT infrastructure for managing containerized applications. However, as the use of Kubernetes grows, so does the security … Read More
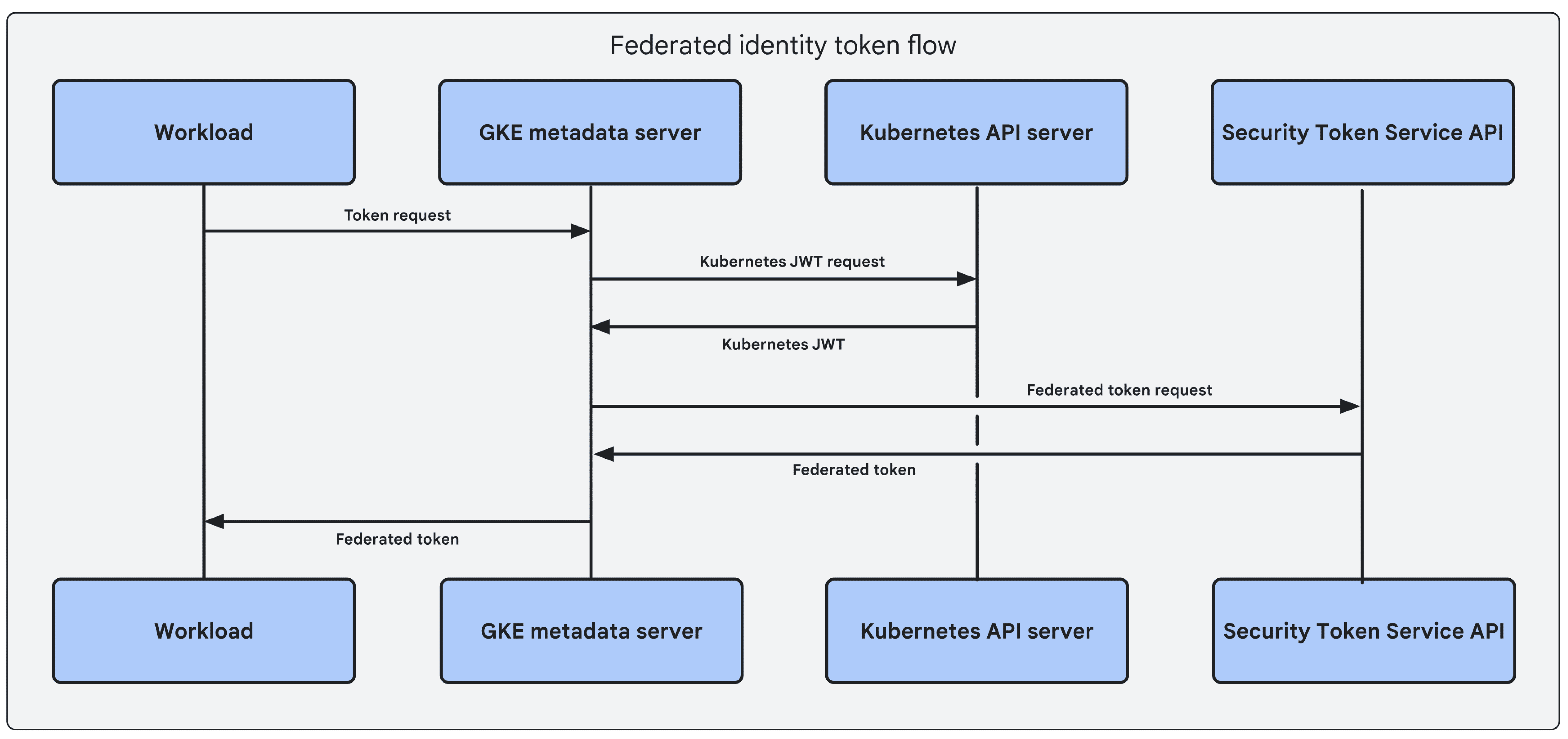
Secure Google Cloud: Identity Federation for GKE
Implementing Workload Identity Federation in Google Kubernetes Engine (GKE) for Enhanced Security and Performance In the rapidly evolving world of cloud computing, securing application access to cloud services without compromising security or flexibility is a critical challenge.Google Kubernetes Engine (GKE) … Read More

System Compromise: Recent Studies on the SolarWinds Incident
The SolarWinds system compromise, a monumental espionage event in recent history, was both intricately designed and executed. Allegedly orchestrated by hackers affiliated with a foreign government, this compromise targeted SolarWinds—a prominent IT management software provider—by infiltrating its widely utilized Orion … Read More

Excellence in Digital Security: The Guilda Commitment
In the rapidly evolving digital landscape, security stands as the paramount pillar supporting the immense structure of modern business. At Guilda, our dedication to excellence in digital security is not just a service we offer—it is the very ethos that … Read More

Securing Trust: Lessons from Banorte Cybersecurity Incident
In the evolving landscape of cybersecurity, securing trust is paramount, as evidenced by the Banorte data breaches which offer a stark reminder of the vulnerabilities that even large financial institutions can face. Through a detailed exploration of these incidents, we … Read More

Digital Integration: Transforming Business Seamlessly
In today’s rapidly evolving digital landscape, businesses face the daunting challenge of keeping pace with technological advancements to stay competitive. At Guilda, we specialize in transforming business operations through strategic digital transformation and digital integration. Our goal is not just … Read More

Enhancing Container Security: Best Practices from Guilda
The Importance of Container Security in Cloud Computing In the rapidly evolving landscape of cloud computing, container technology stands out as a revolutionary tool that reshapes how developers build, deploy, and manage applications efficiently. As organizations increasingly adopt containers for … Read More