Implementing Workload Identity Federation in Google Kubernetes Engine (GKE) for Enhanced Security and Performance
In the rapidly evolving world of cloud computing, securing application access to cloud services without compromising security or flexibility is a critical challenge.Google Kubernetes Engine (GKE) offers a robust solution through Workload Identity Federation, enabling secure and efficient authentication mechanisms for accessing Google Cloud APIs from GKE. This blog post from Guilda’s explores how to implement Identity Federation for GKE, ensuring your applications are both secure and performant.
Preparation Steps for Identity Federation for GKE
Ensuring your setup is correct before you start is crucial. Here’s what you need to prepare:
- Enable the Google Kubernetes Engine API if not already done.
- Update your gcloud CLI to the latest version to avoid common errors and ensure compatibility.
- Verify API Compatibility: Ensure the Google Cloud APIs you need support Workload Identity Federation.
- Enable IAM Service Account Credentials API to manage service account credentials securely.
Setting Up Workload Identity Federation for GKE
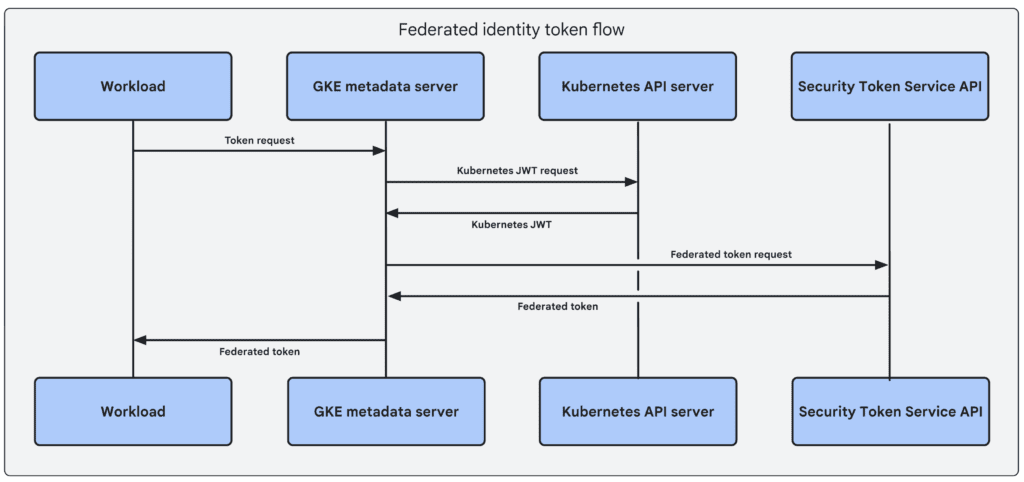
Workload Identity Federation centralizes and simplifies identity management, eliminating the need to manage service account keys for accessing Google Cloud services. Here’s how you can set it up:
- For Autopilot Clusters: Workload Identity Federation is enabled by default.
- For Standard Clusters: You need to enable it at both the cluster level and for individual node pools.
Creating a New Cluster with Workload Identity Federation:
gcloud container clusters create [CLUSTER_NAME] \
--location [LOCATION] \
--workload-pool [PROJECT_ID].svc.id.goog
Updating an Existing Cluster:
gcloud container clusters update [CLUSTER_NAME] \
--location [LOCATION] \
--workload-pool [PROJECT_ID].svc.id.goog
Configuring Your Applications
Once Workload Identity Federation is enabled, configure your GKE applications to authenticate securely to Google Cloud APIs:
- Obtain cluster credentials:
gcloud container clusters get-credentials [CLUSTER_NAME] --location [LOCATION] - Create a dedicated Kubernetes namespace or use an existing one for better isolation and management.
- Set up a Kubernetes ServiceAccount that your applications will use for accessing Google Cloud APIs.
- Bind IAM roles to the Kubernetes ServiceAccount to grant necessary permissions for accessing Google Cloud resources.
Example Command to Bind IAM Roles:
gcloud projects add-iam-policy-binding [PROJECT_ID] \
--role roles/container.clusterViewer \
--member "principal://iam.googleapis.com/projects/[PROJECT_NUMBER]/locations/global/workloadIdentityPools/[PROJECT_ID].svc.id.goog/subject/ns/[NAMESPACE]/sa/[KSA_NAME]"
Verifying and Testing
To ensure everything is set up correctly:
- Deploy a test application that attempts to access Google Cloud resources using the configured ServiceAccount.
- Monitor the application to ensure it can authenticate and perform actions without any issues.
Curious About Securing GKE?
- Have you integrated Workload Identity Federation in your GKE deployments?
- What challenges have you faced in managing identities and access controls in Kubernetes environments?
- How can Guilda’s help streamline your access management for cloud resources to boost security and efficiency?
Why Choose Guilda’s?
At Guilda’s, we specialize in delivering tailored cloud security solutions that safeguard your applications without hampering their performance. By leveraging advanced features like Workload Identity Federation, we help you simplify your security architecture while enhancing your compliance posture.
Whether you’re just beginning your cloud journey or looking to optimize your existing deployments, Guilda’s experts are here to ensure your infrastructure is robust, secure, and ready to meet the demands of modern applications. Contact us today to find out how we can help secure your GKE workloads effectively and efficiently.